Cyber Security

Mission
The Ohio Department of Education Cyber Security Steering Committee will improve upon the information security posture of all School Districts in Ohio, raising their programs to a common level, developing technically-skilled professionals and leaders within the School Districts and Information Technology Centers who strengthen information security through innovative and flexible approaches to implementation.Vision
The Ohio Education Computer Network is a secure, highly available computing environment, designed for the purpose of storing and processing sensitive student information, backed by a nation-leading information security program.Contacts – Who To Call
Your Information Technology Center (ITC) is your first line of defense for cyber security protection. As your technology partner, your ITC relentlessly defends your district from cyber security attacks. If you have a question about cyber security, need help getting started, or need to consult an expert, reach out to your ITC.Multi-State Information Sharing and Analysis Center (MS-ISAC) Cyber Alert Level
These cyber security resources are a collaborative effort of the Ohio Department of Education’s Cyber Security Steering Committee
The Center for Internet Security, the Department of Homeland Security, Filament Essential Services, Information Technology Centers, the Management Council of the OECN, MS-ISAC, OARnet, Ohio CoSN, Ohio Department of Education, Ohio National Guard, and Ohio school districts.
Interactive Incident Map
Map and data provided by The K-12 Cybersecurity Resource Center
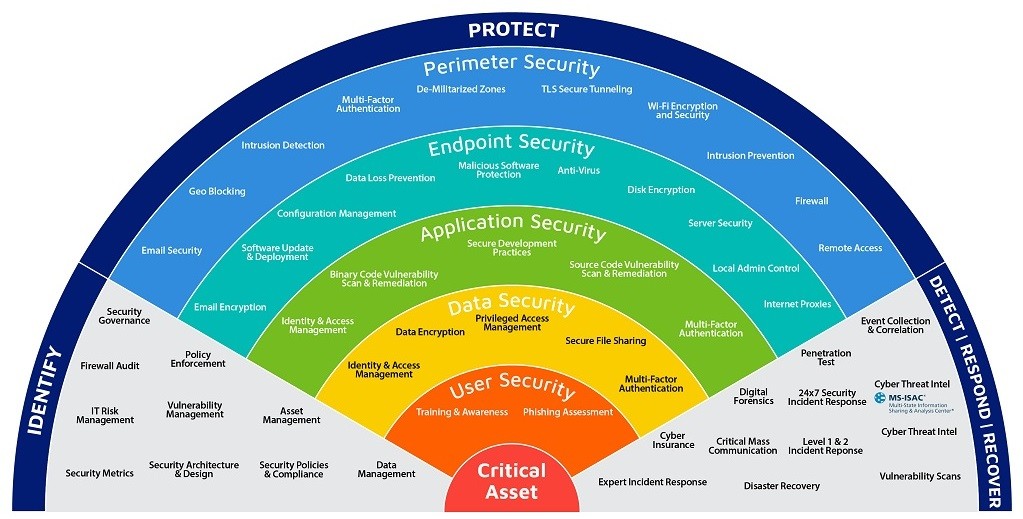
Securities Function Chart
An Information Security Program is a combination of many processes, procedures, and tools that work together to protect the critical assets of an organization. This chart is a visual representation of many of those functions. Ideally, an organization should be able to identify a tool, vendor, or partner relationship that addresses each of these functions.
Identify
- Asset Management
- Inventory of systems
- Account Management
- Strong Passwords
Protect
- Remote Access
- Multi-factor Authentication
- Network segmentation
- Endpoint Protection
- System Backups
- Patching / Maintenance
Detect
- Vulnerability Scanning
- Intrusion detection / Prevention
- SIEM (Security Information Event Management)
Respond
- Incident Response Plan
- Security Awareness Training
- Phishing campaigns
Recover
- Business Continuity
- Restore Systems
- Recovery Planning
- Communication Plans